Abstract
Technology has changed the way we do things and has revolutionized businesses all over the world. The increased use of internet in the process of business transactions, e-business has been hailed as the way to go in the modern and future business growth. This has led to many business enterprises relying on this channel to transact business either with their customer (Business-to-consumer) or with their trading partners (business-to-business). At present, a business plan without e-marketing plans is considered to be headed to a wrong direction, more so to the ones deals in retail business. Basically, the fact that internet can be accessed everywhere in the globe has brought with it numerous challenges, ranging from consumer adaptability to privacy and security concerns. Even though many researchers have attempted to solve this problem, it is interesting to note that they have not focused on some specific aspects such as the implication of e–consumers’ perspective and reactions towards their privacy and security. This is despite many social researches that have indicated that an individual’s privacy and security concerns will determine his or her involvement in any activity. This problem has been adverse in Malaysia considering lack of sufficient studies related to this body of knowledge.
It is known that the customer’s confidence is paramount in the success of business transactions. But how does their lack of confidence in e-tailing affect the retail enterprises in terms of business profitability and success? It is actually the gap of knowledge that the research intends to fill, ensuring that proper and valid information is available to expand the e-retail businesses in Malaysia and elsewhere. It will also provide basis for similar studies that are expected to be undertaken after this study.
Methodology
Quantitative approach to data collection will be used through a valid data collection tool, questionnaire that will be adopted from the past similar studies. The survey questionnaire will have two sections; A & B. Section A will carry 18 questions with details such as demographic profiles of the respondents and level of technology use in e-purchase. Section B will be comprised of 26 questions guided by Liker scales of 1-5, where choices answers such “strongly agree” and “strongly disagree occupying the extreme ends of the choices. This will be backed by open ended questions to ensure consistency and provision of more ‘flesh’ to the research quantitative data. Questionnaire instruments will be tested through pilot study.
Data collection
The data will be collected in Malaysian Institute of Management to achieve the desired diversified respondents. 500 questionnaires will be posted to the identified respondents’ postal addresses. The expected response is placed at the low of 300 (60%) filled questionnaires since the 200 (40%) is expected to cover for the uncertainties. A room for online interview will be left in case of any adverse poor respondents (lower that 60%) and depending on the nimdber of respondents who will show interest in their answer.
Analysis and reporting
SPSS software (available version) is to be used to classify the consumer feelings, behaviors and perceptions in relation to parameters highlighted in the questionnaire; with the support to be provided by the accompanying qualitative data answered in the open ended questions. A report will be provided both in soft copy and hard copy.
Introduction
The rapid technological advancements have significantly changed our lives in many aspects. Some three decades ago no body would have imagined that the world would be ‘narrowed’ the level it is presently, at least virtually. Of all the technological developments, perhaps none has changed the life of human as internet and its components. In the business circles, the proliferation of internet use is evident, with many business enterprises relying on this channel for transactions either with their customer (Business-to-consumer) or with their trading partners (business-to-business). Even though internet use began picking up in the 1980s, its intensive use was realized from the mid 1990s, when quite a number of businesses adopted internet as a primary means in all levels of transactions. It is evident that presently, most business plans cannot go without mentioning strategies for e-marketing. Principally, the ability of internet to penetrate the corners of the globe has brought with a wide range of challenges, ranging from consumer adaptability to legal and security concerns (Clarke, 1988; Goldsmith & Bridges, 2000).
This phenomenon has created wide range of interest among research scholars. However, it is interesting to note that majority of the researchers have mainly focused on the consumer’s ability to consume through online purchase; how technology has revolutionized the whole range of business sector; and how to maximize its usage for the buzzword, competitive advantage (Grabner-Krauter & Kaluscha, 2003; Joines, Scherer & Scheufele, 2003; Singh & Hill, 2003). This could be widely associated with the principle of maximum profitability that majority of business, if not all operate from. But to they receive maximum with their e-retailing? Is the opportunity optimized? Despite the fact that privacy and security concerns related to e-commerce have been with us for quite a long time, brief overview of the research papers and other scholarly materials clearly shows that majority of them are non-exhaustive in matters security and privacy. In short, just a handful of the material touches slight issues as concerns internet use privacy and security without much detail. The reason behind this lack of interests is unknown. The impact of this lack of body knowledge is that businesses do not have clear information on how much they lose, from the potential e-buyers’ perspective.
Privacy of an individual is as important as any activity related to the person involved in the activity (Udo, 2001). Many scholars and observers have acknowledged that privacy and security issues will determine the future of the business and technology as regards to online (Udo, 1997; Westin, 2001; Ricciuti, & Evers, 2007). Business information sector studies clearly show that many studies have concentrated on the nature and size of the business volume that the e-retail can drive (Ricciuti & Evers, 2007), and have inadvertently ignored the fact that security issues are barriers to its potentiality (Miyazaki & Fernandez, 2001). Flavian & Guinaliu (2006) observe that most of the business case studies do not look in much detail how much businesses they lose due to the concerns raised by buyers, how many retail buyers do not purchase through online means and how much this has impacted on the business profitability. In fact such trends are global interestingly, they touch almost all corners of the world, Malaysia included. Malaysia as a country belongs to the international community and it has adopted the e-retail just like any other countries of the world. This study intends to investigate the Malaysian online buyers’ attitude towards their privacy and security concerns and how this will impact on their intention or willingness to buy retail products online. Their views and perspectives on the best way forward will be paramount in an attempt to add to the body of knowledge the missing link between the retailers and buyers. Recommendations drawn from the customer’s perspective and the quantitative research findings will be provided, giving a clear and coherent plan on what should be done to solve the puzzle.
Background to Research
Even though e-retail has boosted the economies of the world, failure by many organizations and business entities to provide secure transaction process has damaged the e-business reputation due to lost confidence among the parties involved (Flavian & Guinaliu, 2006). Many governments have therefore supported the idea of enacting legal framework to boost e-business through confidence building. This is after noticing the potentiality that is within the e-business for their respective economies.
Malaysia has experienced some of the widest range of matters as concerns legal aspects of e-business (Flavian & Guinaliu, 2006). According to Fried (1998) electronic self governance requires that there exist a trust built among the players in order make them entrust each other with information. He therefore highlights some three key components for safe communication between the parties involved as: That each party is assured of the identity of the communicating parties, that the two parties are confident that there is integrity in the transaction process and the transacted business and that the transacted business can never be refuted (Fried, 1998). The Malaysia legislature passed the Digital Signature Act 1997 (Aladwani, 2001), thereby giving the government opportunity to implement Public Key Infrastructure framework (DSA, 1997 cited in DeSilva, 2003). PKI is meant to assist cryptography services since it contains policies as well as procedures to put efficiency in the management of key and certificates for the security communication (DeSilva, R 2003).
Successful E-retail Models
In mid 2000, the government of Malaysia approved the Bank of Nagara’s proposal to allow internet banking by the commercial banks (BNM, 2005). To date, just a handful of banks in Malaysia are allowed to offer internet banking services to its customers, with the Banking and Financial Institutions Act of 1989 as well as Islamic Banking Act of 1983 as the basis for guideline (BNM, 2005). Before this period, a few Malaysian banks like PhileoAllied Bank offered e-banking to its clients through the use of proprietary Software and Connection to the Banking (DeSilva, 2003). The bank transacted business through its PLDIRECT/ PALWORLD Proprietary system (DeSilva, 2003). The hallmark of all e-banking services came when PhileoAllied and Malayan Bank to create one of the biggest e-banking ever, through their “MayBank2u” service provider joint venture (Ng, 2002). After only two years, the number of banks transacting their businesses through internet has doubled, from 6 to twelve (Ng, 2002; DeSilva 2003).
DeSilva (2003) observes that despite the increased number of banks offering their retail services through internet, it was evident that banks had more benefits as compared to customers. The critical aspect that was noticed is that many customers were skeptical about e-banking services, expressing their concerns with the security of their details. This jeopardized the acceptance. According to Ajzen (2006), the expression of confidence and acceptance of the internet banking system still remain a critical factor to ensure its progress. Mckinsey & Company cited in Kostakos, O’Neill, Little, et al. (2005) reported that only 31% of Malaysians had interest of using internet as a channel for retail banking, while a whooping 66% were not confident about the security of the whole process. Other related countries like Singapore, Thailand, China, and Hong Kong, it is reported that the e-retail in banking are still either in its infancy stage or majority of the customers had not approved of it (Kostakos, O’Neill, Little, et al., 2005; Hoffman, Novak & Peralta, 1999).
Even through in theoretical terms we do have no basic need to connect the e-tailing services with the banking services electronic banking, there is a strong possibility that fraud may occur whenever an e-tailer give his or her personal details to the bank of transactions. In short the interconnection between two banks may be treated as not part of the internet but in essence it is an intranet (Joines, Scherer & Scheufele, 2003). It therefore means that whenever such a transaction occurs, there is no barrier into what will limit anyone within the system access any of the information (Joines, et al., 2003).
Tesco.com is the e-retail branch of the 3rd largest global grocery retailer; Tesco Plc. Established in 1996, Tesco.com is currently the world’s largest e-retailer, with annual growth rate of 30%. Its success is attributed to among other areas, its well designed secure website with a lot of functionality, getting continuous support from 130 servers which make it reliable and accessible. In his case study of Tesco and Webvan, Drew (2005) outlines that the reason why Tesco.com is successful in is because of its business model where all its online activities are integrated with its parent company Tesco, hence creating the needed confidence that its e-retail is valid. This was a complete contrast with its counterpart Webvan that made its online retail more of a separate venture, where things like price were reduced for online retail, subsequently creating suspicion among shoppers that the online deal is not legitimate (Drew, 2005). This same integrated model of e-retail and on-shelve retail business is applied by Wal-mart Inc., an American based chain of retail stores which has been branded the world’s largest public corporation in terms of revenue (Drew, 2005). In a more advanced level Wal-Mart has also pioneered the use of warehousing as well data mining in its e-retail branch of business, a venture that is believed to its continuous efforts to make transaction and data store safe (Drew, 2005).
Amazon.com has a very explicit privacy policy as observed by Bhattacharjee (2002). After his empirical study of the trust perception people have on Amazon, he concluded that Amazon can generally be entrusted with users’ private data that they get access to during transaction (Bhattacharjee, 2002). Amazon.com’s private policy clearly states that the company applies Phoenix Model Policy (Bhattacharjee, 2002). At present, e-bay.com is one of the leading outfits dealing in e-business, after the company was created from its parent company ebay. The online version e-bay.com is said to contribute to a half of its revenue, hence putting confidence on the management’s strategy of focusing their online business on the customers’ own perspective (Fried, 2009).
In Malaysia posonline.com has proved that a security of information is very critical for the growth of business. The company has centralized all its information exchange process that deals with their customer transaction details, thereby making it easy to manage the storage process, help them organize and distribute its services (Bhattacharjee, 2002; Fried, 2009). This is in contrast to many scenarios where people email their details facing the risk of losing privacy to hackers. Another critical online retailer is muda.com (Fried, 2009). The Malaysian online company that deals in online sales and advertisements has a strict policy for its e-business. Some of its policies to reduce online cheats are by stating categorically that all links and images of property that are given for the advertised property must be valid (muda.com, 2009). Other restrictions are placed on illegal and/ or prohibited goods, offensive contents, unrealistic offers, etc (muda.com). Other companies that have created related business models are like amway4u.com and lelong.com which have realized that e-retail relies on the customers’ perspective (Bhattacharjee, 2002).
Proposed research model
Many researchers have adopted extension of TAM in their respective studies to introduce and measure the impacts and acceptance of the use of information system in an effort to draw independent variables. Grabner-Krauter & Kaluscha (2003, cited in Jutla & Bodorik, 2003) used it to extend their perceived notion that the whole concept of e-security is perceived variables. Amaoko- Gyampah & Salam (2003, cited in Van Slyke, et al., 2006) projected their claim that any research that is devoted to the extension of TAM is purely an attempt to examine the antecedents of the particular two belief theories that defines TAM. Wixon & Todd (2005, cited in Van Slyke, et al., 2006) also belief that researchers have attempted to introduce TAM basically in one of the three main channels; by the introduction of factors from the related model, by the introduction of another similar or almost similar belief, or just adding other belief, and/or by an examination of the antecedents as well as moderators of a particular perception in relation to usefulness or importance because it is taken as easy to use.
Considering the above basis the extended adoption of TAM as a theoretical model is basically to help in measuring external variables on the e-retail. The other major reason is that it has been proven to be a simple model (Van Slyke, et al., 2006) that can be applied to such kind of study where many users of e-retail are expected to be examined.
This research model proposed is illustrated in the figure below. Just like other studies, the extended use means that variables like the perceived security and privacy (PSP)- external variable, perceived care (PC)-independent variable, how much they value their security (Perceived value, PV)-independent variable, Intension to purchase (PI)-dependent variable
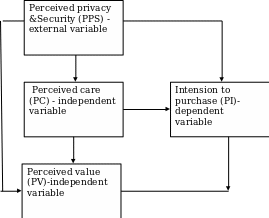
Privacy and security
However, several studies still reveal that lack of confidence and skepticism about e-retail is till rampant and that it should never be assumed just because some few businesses have succeeded (Grabner-Krauter & Kaluscha, 2003) Grabner-Krauter & Kaluscha (2003) say that the whole process of internet purchase by the customers look simple and easy, but both the people who have developed the programs and the business owners knows exactly this whole process goes through many persons’ scrutiny, hence creating a security concern. Furthermore, global retailers have done little to deal with the security and legal issues that concerns e-retail (Chen & Barnes, 2007; Laudon & Laudon, 2001). That is, there are evidently insufficient laws and regulations to guide or monitor the global e-commerce. Other studies also reveal that many customers are not willing to divulge their detailed information via internet business transactions, and those who are ready to do so are only expecting to win some prices on offer (Ratnasinghan, 1998).
The study of any social science intimates that privacy of an individual is as important as any activity related to the person involved in the activity (Laudon & Laudon, 2001). It is widely accepted to be an issue that will determine the future of the technology related to online business transactions it has the ability to affect the attitude and perceptions of the trading parties, especially the buyer. In the field of business information, it is evident that quite a number of studies have concentrated on the nature and size of the business volume that the e-retail can drive (Flavian & Guinaliu, 2006). This problem has been compounded by the fact that quite a number of researchers have had conflicting concepts as regards security, mostly concerned with the interest of the business (Flavian & Guinaliu, 2006). Ricciuti & Evers (2007) observe that many of the literature available are case studies of businesses, which in actual sense do not look much into the consumer’s privacy in essence but are interested in finding how to assure e-consumers of their security.
Even though it is acknowledged that quite a number of studies have not done much on the impact of privacy and security issues affect businesses. However, some research studies have seen the gap and recommended, albeit with little touch the need to have this issue looked at in future studies. For instance, Stanton & Weiss (2000) researched on the value of e-monitoring, concentrating both on the views of the employee and the employer perspective. [For methodology see Santon & Weiss (2000)]. In fact the authors of the study pointed out the need to look at the issue on the perspective of the buyer, to find out how it impacts on the overall business model and profitability. They argue that one critical issue that remains to be looked at is the impact that is brought about by the employees’ skepticism over the internet business has on the overall profitability of the business (Santon & Weiss, 2000). This is after an initial study that revealed that many consumers were not sure of their security when purchasing products through the internet, with some highlighting the discrepancies in price and possible fraud through one’s personal detail (Ratnasinghan, 1998; Ajzen, 2006).
Problem Statement
Technology has spurred the growth of business throughout the globe, opening up new business opportunities. It is evident that many retailers have adopted the e-transaction between them and their customer, creating a model of business that is mercurial in nature. However, it is also apparent that issues related to privacy and security has hindered many consumers from accepting the new trend, preferring to do business through traditional on-shop approach (Ricciuti & Evers, 2007); Xinhua News Agency, 2009). It is also acknowledged that the responsibility of restoring the customer’s confidence through adequate security measures lies with the government and the retailers, and not the customer’s. But much of the case studies, ostensibly sponsored by these business enterprises have mainly concentrated on how to boost online sales in general terms, only touching on the privacy and security as a fringe concern in their analysis and reports. So an average effort to establish how much these retailers lose by not taking privacy and security matters seriously is worthwhile.
Research Objective
The objectives of this research are:
- To establish the attitudes of the online buyers as concerns their privacy and security.
- To establish how their concerns or lack of concerns impact on the retailers ability to maximize their business potential
- To establish their views and perspective on what should be done to bring confidence in the process of exchanging their personal information virtually with retailers.
- To recommend on what should be done ensuring the e-buyers gain confidence on the e-transaction process.
Research Questions
The following key questions will guide the research process:
- What is their Malaysians’ perception on e-retailers security level?
- How much are the Malaysian e-buyers care about their privacy and security, how much are they concerned?
- How does their privacy and security concerns affect their intention to buy or their willingness to buy through online?
- What are their views on what should be done to boost their confidence so as to make them buy online?
Significance of Research
As indicated in the research background, it is clear that many researchers have done little to unlock the barrier in achieving maximum retail business potential through on-line research. This research is a derivative of a theoretical background of many researches that have identified how much has not been done in the process of bringing confidence among online retail buyers in Malaysia. This is because the customer’s perspectives have not been included in the various research undertakings in Malaysia. In fact, many research undertakings have not looked specifically on the impact customer’s privacy and security concerns will have on the business models and profitability after projections, hence creating a gap in knowledge (Stanton & Weiss, 2000; Grabner-Krauter & Kaluscha, 2003). Furthermore, Malaysian researchers have not taken much interest in researching on this issue, a phenomenon I noticed through my literature search. The confidence to use researches from other regions is due to the global nature of e-retail, a boundary-less trading channel (Morris & Venkatesh, 2000; Laudon & Laudon, 2001). It is this gap that this research will seal, ensuring that a proper and valid information is available to expand the e-retail businesses in Malaysia and elsewhere. It will also provide basis for similar studies that are expected to be undertaken after this study.
Literature Review
As earlier observed, trust is a very critical aspect in the e-business, especially to the consumers. Hoyer & MacInnis (1997) observe that consumer trust is determinant of the perceived risk. Miyazaki & Fernandez (2001) researched about the security seals provided by specific companies in an attempt to assure the e-consumers of their security. Their study revealed many organizations have adopted the use of several techniques to assure their consumers that their personal details on e-tail process are safe. The companies apply such techniques as company logo or seal programs (Miyazaki & Fernandez (2001). Udo (2001) conducted an online survey to establish the consumer’s perception about the privacy and security issues on their personal details transactions. The study revealed that many e-retailers ranked privacy as their major concern a head of other concerns, with their major worry being the possible use of their personal details for other use outside their intended purpose (Udo, 2001. The interesting part of the survey result is that only 3 out of ten e-buyers were not bothered much by the privacy and security of their, living the seven others with most worries and that they are just doing e-trade even though they are aware of the risk associated with it (Udo, 2001). The researcher therefore concluded security and privacy are indeed the main barriers to the success of e-commerce (Udo, 2001).
Sheehan (2002) on the other hand conducted a survey to establish the level of concern that e-consumers have concerning their security and privacy. He unlike other researches fragmented his group of respondents into pragmatic, unconcerned and privacy fundamentalists on the e-commerce users to give her direction on the degree of concerns as per these groups (Sheehan, 2002). This result revealed that a whooping 81% of the respondents were actually pragmatic about their privacy issues, the unconcerned represented 16% and finally the fundamentalists took a mere 3% (Sheehan, 2002). According to Sheehan (2002) this result clearly revealed that the privacy concerns are actually a result of the context in which the consumers view things and not a permanently embedded “psychological construct” within a particular individual. It therefore showed that it is something that can be changed and reconstructed.
In an attempt to analyze the theoretical aspect of the consumer behavior towards e-purchases, Singh and Hill (2003, cited in Van Slyke, et al., 2006) approached their study with the analysis of two theories: social contract theory and stakeholder theories. The study was based on the German e-retail buyers, analysis of their attitude towards their concerns on matters their security (Van Slyke, et al., 2006). The researchers applied likert scale’s 5-point to reveal their attitude towards online purchase of items (Van Slyke, et al., 2006). In their findings, they reported that almost the entire respondents wanted the issue of internet security handled with caution as they were not confident with their revealed personal identities (Van Slyke, et al., 2006). It again exposed the role of the e-retailer together with the government to ensure the matters of security are sorted out.
Critically, it is evident that all the above highlighted studies have not touched in any way the level of impact this skepticism has in terms of willingness to partake e-purchase transaction. Whilst it is good to acknowledge their importance, it is evident that there is a big gap in literature as concerns knowledge of this important area of research.
One study that came close to unlocking this area was done by Van Slyke et al. (2006). The study concentrated on the level to which people regard their privacy and how this influences their readiness to do transaction through the internet. The study methodology concentrated on the level in which people handled their personal details on the internet as regards the level of value placed on each website, i.e. well known websites and little known ones (Van Slyke, et al., 2006).
The finings revealed that the popularity of a website is a determinant of the way the consumers will handle the security matters of the web, i.e. determine which information to put on which website (Van Slyke, et al., 2006). However, it is critical to note that this study did touch on the general people and general websites, not e-retail. Of course it can be intimated that the way people treat business transactions is different from the way they treat social issues on the internet. This is open for comparison once this study is accomplished.
In more practical environments, the concerns were similar. Jutla & Bodorik (2003) did a case study of VerticalNet business model. Their findings was that the company’s business to business models (B2B) failed because of lack of trust in the e-transactions, emphasizing that businesses do not have confident in a third party storing their information about the transactions (Jutla & Bodorik, 2003). Kaufman & Powers’ (2002) study on the IBM e-business model revealed that the success of the company is based on its early realization and adoption of “customer-empowered” privacy management in the application of cookie crushers. They further highlighted other ways of empowering the customer through such secure and user-friendly software like anonymizer, P3P preference document among other software (Kaufman & Powers’ (2002). Ajzen (2006) investigations on the Microsoft’s failed business initiative code-named HailStorm service revealed that users of the security gadgets or software demand full control of them to an extent that failure to give that will make them shy away from your business. They are putting a lot of emphasis on this fact that all these is as a result of the users’ continuous interest in self-control of personal data (Ajzen, 2006).
Evidently, many studies tend to merge the issues together with other parameters in their respective studies. Joines et al. (2003) researched on the motivational factors associated with individuals’ demography to the security and privacy concerns. Sheehan (2002) on the other hand studied specific factors affecting the decision by the consumers to purchase through internet. Still most of the studies that are related to adoption of technology only focus on the privacy and security together with variables (Sheehan, 2002). Furthermore, the studies do not have concrete evidence of having investigated the impact of security and privacy on the retail business.
Methodology
Design of the Survey
For this research, quantitative approach will be applied where questionnaires will be used as the main survey instruments. The design of questionnaires will be adopted from the other previous related studies in the e-marketing, and the contents will be modified to fit my research question. For example, during the literature search, I identified some items that reflected some similarity with my research objective, thus the intention to selectively adopt such materials. This in line with Sekaran (2000, cited in Stanton & Weiss, 2000), who noted that it is important for the selected items to reflect on some specific concepts by which the overall generalizations are to be drawn, to ensure the validity of the content.
Sections of the survey
The first part of the survey will entail two sections; section one will have 18 questions related to respondent demographic profile, the respondents level of technology usage. This section will be concluded by two specific open ended questions that will ask the respondent the reason why they use online purchase as a means of buying their goods through online means.
This part will be comprised of 26 questions. Likert scales will used to get the opinions of the respondents, where they will be asked to give their answers in a structured scale of 1-5. In this part, points like “strongly disagree” will be in a scale of 1, and “strongly agree” scale five. Some other questions in this section will take the format of concern expression where participants will be asked to rate the level of their seriousness in a scale of 1-10, with 1 representing the idea that their decision is not serious in anyway while 10 indicating that the issue absolutely serious. This last question is meant to expose any intention to use e-retail by the customers. It is also expected to show some levels of consistency in the items selected for the research question. This is in line with the notion that numerous factors will drive the desire to adopt e-buying decision by a customer (Aladwani, 2001). He emphasizes that external challenges are abound for any organization with an aim of adopting advanced technology in their trade. In this case external factors are represented by customers (Aladwani, 2001). Being aware of the limitations of Likert scale in providing only “yes” and “no” answers, open-ended questions will largely follow the scale’s brief statements to give it the necessary flesh and freedom of expression in the respondent’s own words. As Acquisti (2002) observes, “Likert scale is a skeleton that is useless without flesh” (p.187)
Data collection
To collect a wide range of data in terms off demographic as well as gender orientation, I will use stratified samples from Klang Valley with concentration in major cuties (i.e. Kuala Lumpur and Petaling Jaya). This is intended to ensure the survey covers a wide range of respondents, especially the internet users and e-customers. This in line with Cheung & Lee’s (2001) findings which indicated that a typical e-retailer is mostly educated lot, especially the once who have got tertiary level qualifications in their areas of specialization and practically below the age of 35, and most of all majority city dwellers.
The distribution of the questions will be conducted through mail, i.e. posting the questionnaires into the 500 selected potential respondents’ mail box. However, the uncertainties are taken care of as not all respondents are expected to post back completely answered questionnaires. The target response is 300, so the 200 plus questionnaires are meant to take care of the expected unreturned mails as a result of any uncertainty. This means that 60% response rate is expected. This is idea is derived from a similar survey in a similar setting and design, which gave a 60% response (See Aladwani, 2001.). At the end of the questionnaire, the participants will be asked if they are interested in conducting an online interview or not. This is expected to give a clue of whether it will be necessary to do that, just to cover all demographic groups.
Analysis
Data analysis will be conducted with the help of SPSS software (available version) to classify the consumer feelings, behaviors and perceptions in relation to parameters highlighted in the questionnaire; with the support to be provided by the accompanying qualitative data answered in the open ended questions. Cheung & Lee (2001) observe that SPSS is very critical statistical software for analyzing social data, and because social data defines business, a business research will rely on SPSS. This may explain the common trend where most of the business researchers use this statistical package to analyze their quantitative data.
A pilot study will be carried out to test the questionnaire instruments and adjustments will be made where appropriate to ensure an all inclusive and focused data is collected. This is intended to validate the whole contents of the questionnaire, i.e. by exposing the correctable weaknesses prior to the study (Cheung & Lee, 2001; Keynes, 2004).
Methodology Limitation
Even though it is expected that the response rate will be 60% (to the minimum), any form of uncertainties are expected because of the wide range of demographic nature of this study in terms of age, gender, social position in the society. Most of the previous similar studies restricted their target response to ages below 35 (Aladwani, MA 2001). The intention to make it open up to all sets of age groups of up to 60 years is expected to generate with it the potential non-response, especially from the older generation of the Malaysian families who tend to be more conservative in their ways of purchase. In fact this is the reason given for lack of inclusion in most of the similar studies involving technology use (Aladwani, 2001). But to this study, it will be important as it will help answer the research question, if indeed technology hinders e-retail, on the customer’s perspective. Theoretically, non-response may also be as a result of lack of commitment from the intended respondents. The 200 questionnaires (40%) are likely to help solve any emerging issue in relation to non-response.
The other hypothetical problem is that the current generation wants to identify with paperless activities, i.e. they would rather answer online questionnaire rather than peruse through a big volume of printed version of the questionnaire. This may lead to some incomplete answers to some questions, hence increasing more problems. In case such a scenario is experienced, a stratified online research will be conducted to ensure the group is not left out. This will only take place if the group answers some questions and from it, a trend is shown of an interest in doing online interview.
Reference
Acquisti, A. (2002). Protecting Privacy with Economic: Economic Incentives for Preventive
Technologies in Ubiquitous Computing Environment Workshop on Socially-informed Design of Privacy-enhancing Solutions in Ubiquitous Computing: Ubicomp.
Ajzen, I. (2006). Attitudes, Personality, and Behaviour, Open University Press.
Aladwani, M. A. (2001). Online banking: a field study of drivers, development challenges, and expectations. International Journal of Information Management, vol. 21, pp. 213-225.
Bhattacharjee, A. (2002). Individual Trust in Online Firms: Scale Development and Initial Test. Journal of Management Information Systems, Summer 2002, Vol. 19, No. 1, pp. 213-243.
BNM. (2005). The Central Bank of Malaysia, List of Licensed Banking Institutions in Malaysia. Web.
Chen, Y., & Barnes S. (2007). Initial Trust and Online Buyer Behaviour. Industrial Management and Data Systems, 107 (1), 21-36.
Cheung, C. & Lee M. (2001). Trust in Internet Shopping: Instrument Development and Validation through Classical and Modem Approaches, Journal of Global Information Management, 9(3).
Clarke, R.A. (1988). Information Technology and Dataveillance. Communication of me ACM, 31 (5), 498-512.
DeSilva, R. (2003). Maybank on track with Internet banking service, News Straits Times, Management Times Section.
Drew, S. (2005). Why business models matter, and how they make a difference in internet commerce. Learning Resource Center, The Make and Break Issues in IT Management. Journal of Information Management, (3), Vol.3, pp. 140-142.
Flavian, C., & Guinaliu M. (2006). Consumer Trust, Perceived Security and Privacy Policy: Three Basic Elements of Loyalty to a Website. Industrial Management and Data Management, 106 (5), 601-620.
Fried, C. (1998). Privacy. Yale Law Journal, 77 (1), 475-493.
Fried, I. (2009). PayPal will be bigger than eBay.com. Web.
Goldsmith, R., & Bridges E. (2000). E-Tailing versus Retailing: Using Attitudes to Predict Online Buying Behavior. Quarterly Journal of Electronic Commerce, 1 (3), 245-253.
Grabner-Krauter, S., & Kaluscha E. (2003). Empirical Research in Online Trust: A Review and Critical Assessment. International Journal of Human Computer Studies, 58 (6), 783-812.
Hoffman, D.L., Novak, T.P. & Peralta, M. (1999). Building Consumer Trust Online, Communications of the ACM, 42 (4), 80-85.
Hoyer, W.D., & MacInnis D.J. (1997). Consumer Behaviour. Boston: Houghton Mifflin Company.
Joines, L., Scherer L., & Scheufele A. (2003). Exploring Motivations for Consumer Web Use and their Implications for E- Commerce. Journal of Consumer Marketing, 20 (2), 90-108.
Jutla, D., & Bodorik P. (2003). A client-side business model for electronic privacy. eTransformation. Slovenia: Bled.
Keynes, M. (2004). Clarifying the effects of Internet Monitoring on Job Attitudes: The Mediating Role of Employee Trust. Information and Management, 43 (7), 894-903.
Kostakos, V., O’Neill E., Little L., & Sillence E. (2005). The Social Implications of Emerging Technologies. Editorial/ Interacting with Computers, 17, 475-483.
Kaufman, J., & Powers C. (2002). IBM Classic e-security arrangements. Journal of Internal business (2), 234.
Laudon, K.C., & Laudon J.P. (2001). Essentials of Management Information Systems: Organisation and Technology in the Networked Enterprise, Prentice Hall, 4th Ed.
Miyazaki, A.D., & Fernandez A. (2001). Consumer Perceptions of Privacy and Security Risks for Online Shopping. The Journal of Consumer Affairs, 35, Summer, 27-44.
Morris, M.G. & Venkatesh V. (2000). Age Differences in Technology Adoption Decisions: Implications for a Changing Workforce. Personal Psychology, 53 (2), Summer, 375-403.
Muda.com (2009). Muda.com.my is a Malaysian market place for buying and selling online. Web.
Ng, J 2000, ‘Banking online’, Personal Money Magazine on Managing Your Finances, no. 11, The Edge Malaysia.
Ratnasinghan, P. (1998). Trust in Web-based Electronic Commerce Security. Information Management and Computer Security, 6 (4), 162-168. MCB University Press. Web.
Ricciuti, M. & J. Evers (2007). “Solving the Web security challenge,” CNET News, Web.
Sheehan, K.B. (2002). Towards a Typology of Internet Users and Online Privacy Concerns. The Information Society, 18, 21-32. Web.
Singh, T., & Hill, M.E. (2003). Consumer Privacy and the Internet in Europe: A View from Germany. Journal of Consumer Marketing, 20 (7), 634-651.
Stanton, J.M., & Weiss E.M.(2000). Electronic Monitoring in their Own Words: An Exploratory Study of Employees’ Experiences with New Types of Surveillance. Computers in Human Behavior, 16 (4), 423-440.
Udo, G.J. (2001). Privacy and Security Concerns as Major Barriers for E-Commerce: A Survey Study. Information Management and Computer Security. 9 (4), 165-174.
Van Slyke, C., Shim J.T., Johnston R., & Jiang, J. (2006). Concern for Information Privacy and Online Consumer Purchasing. Journal for the Association of Information Systems, 7 (6), 415-444.
Westin, A. (1997). Privacy and Freedom. Ateneum, New York. Xinhua News Agency. (2009). Malaysia mulls over developing retail sales index. Web.